The Department of Homeland Security (DHS) workforce has become increasingly mobile, driving the need for secure mobility solutions and a coordinated approach and framework to guide the selection and implementation of common enterprise mobility solutions. To accelerate the safe and secure adoption of mobile technology within DHS and the federal government, the DHS Science and Technology Directorate (S&T) created the Mobile Security research and development (R&D) Program.
Mobile Security R&D Program Goal: “Accelerating the adoption of secure mobile technologies by government and industry to enable the homeland security mission.”
The Mobile Security R&D program has three efforts address in R&D:
- Mobile Device Security
- Mobile Application Security
- Mobile Network Infrastructure
Watch Video Now!
Motivation
Our dependency on mobile technology makes it an attractive and lucrative target for cyberattacks. A broad range of threats now challenges both government and consumer mobile devices. The government faces additional threats from advanced nation-state actors. Additionally, attacks can also focus on and jeopardize government employees’ physical wellbeing, finances, or privacy. Moreover, a security compromise of both the government and government employee’s mobile systems can lead to unauthorized access to, change of, or destruction of government functions.
The key developments in mobile threats include the following:
- The mobile ecosystem is complicated because it is comprised of different original equipment manufacturers (OEMs), operating systems platforms, application development tools, mobile network infrastructure, and much more. The complex and varying degree of inter-dependencies within this ecosystem makes for a broad and varied attack surface that presents unique security challenges for mobile technology users.
- Malware has grown substantially in the U.S., driven by an increase in threats that hold devices and their data hostage in exchange for payment (ransomware).
- Mobile threat sophistication is increasing. Malware has entered the marketplace pre-installed on certain devices thereby compromising the supply chain. Mobile-based malware now employs sophisticated self-defense techniques, such as evading attempts to detect and defeat the malware.
Mobile network infrastructures face unmitigated attacks. Reports suggest protection mechanisms are rarely implemented in carrier infrastructure, and there is limited ability to protect against geolocating users through their devices. The geolocation risk is exacerbated by legal global roaming partnerships between carriers.
Approach
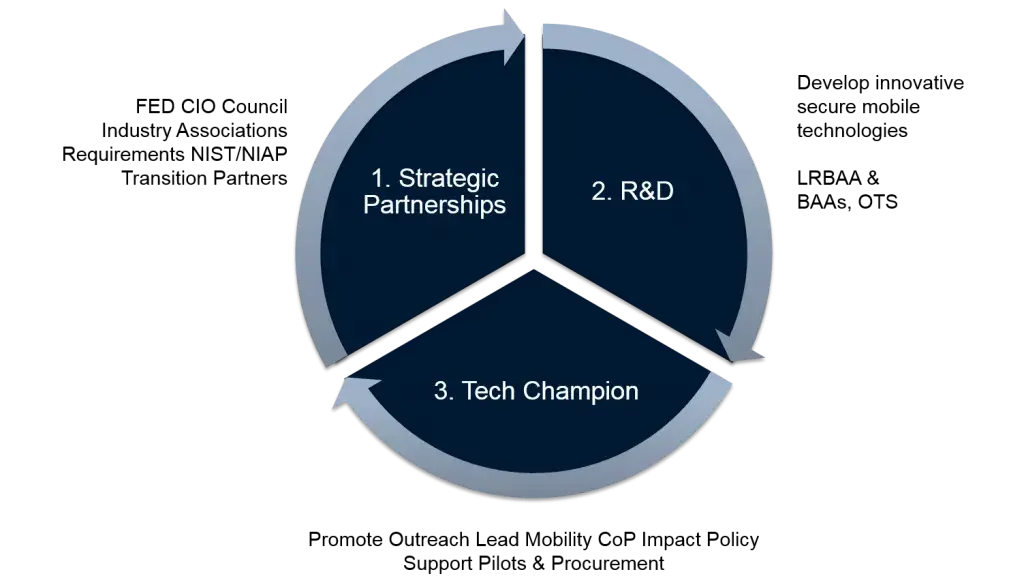 To respond to these evolving threats and security challenges, S&T’s CSD has developed and will transition programs to accomplish several strategic objectives and initiatives. Through this work, S&T will ensure DHS is poised to bridge current capability gaps and deploy solutions that effectively, efficiently, and securely enable the DHS mission. The Mobile Security R&D program has established three overarching objectives to achieve its vision: strategic partnerships; research and development (R&D); and tech championing.
To respond to these evolving threats and security challenges, S&T’s CSD has developed and will transition programs to accomplish several strategic objectives and initiatives. Through this work, S&T will ensure DHS is poised to bridge current capability gaps and deploy solutions that effectively, efficiently, and securely enable the DHS mission. The Mobile Security R&D program has established three overarching objectives to achieve its vision: strategic partnerships; research and development (R&D); and tech championing.
Objective 1: Partner with DHS components and federal stakeholders to identify operational requirements and capability gaps.
The Mobile Security R&D program leverages the efforts of existing federal and DHS mobility working groups to gather and prioritize remediation of mobile security capability gaps preventing mobile implementations both at the federal level and across the Homeland Security Enterprise (HSE). These groups include the following federal and DHS working groups:
Federal Interagency Working Groups:
- Federal Chief Information Officers (CIO) Council’s Information Security and Identity Management Committee (ISIMC) Mobile Technology Tiger Team (MTTT)
- ISIMC Identity, Credential and Access Management Sub Committee (ICAMSC)
- Mobile Services Category Team (MSCT)
- MTTT Mobile Application Security Vetting Working Group
DHS Mobility Working Groups:
- Mobility Initiative-5 (MI-5)
- Mobile Community of Practice
- President’s National Security Telecommunications Advisory Committee (NSTAC) Network Security Information Exchanges (NSIE)
Objective 2: Develop innovative, secure mobile solutions to enhance the DHS mission.
The Mobile Security R&D program has established several initiatives with private industry and academia through long-range Broad Agency Announcements (BAAs), targeted BAAs, Small Business Innovation Research (SBIR) funding, and Other Agencies Technology Solutions (OATS) SBIRs. S&T has awarded mobile technology research contracts to address primary gaps identified through its partnerships with other DHS components and federal agencies. These efforts address needs in three R&D areas:
- Mobile Device Security
- Mobile Application Security
- Mobile Network Infrastructure
Objective 3: Champion the technology created by the program to support its transition into operational practice.
Transitioning the developed technology into operational use is an integral part of the Mobile Security R&D Program. Starting with the first objective, we engage stakeholders early to help drive research and identify customers that are able to be in involved. During and after research execution, the Mobile Security R&D Program conducts outreach to educate and raise awareness of the innovative technologies being developed by the program. Outreach activities include hosting technology showcases, engaging directly with federal CIOs, engaging in matchmaking, and facilitating pilot projects to promote early adoption of a technology.
Resources
For the latest information about S&T Cybersecurity, visit the S&T Cybersecurity News, Publications, Videos and Events pages.
Publications & Fact Sheet
- Automating National Information Assurance Partnership Requirements Testing for Mobile Apps Report
- DHS Study on Mobile Device Security
- Evaluating Mobile App Vetting Integration with Enterprise Mobility Management in the Enterprise
- Mobile App Security Study: Securing Mobile Applications for First Responders
- Mobile Security R&D Program Guide, Volume 3
- Mobile Device Security Fact Sheet
