The Identity Management research and development (R&D) project provides government program managers with the R&D expertise and resources needed to enhance the security and trustworthiness of their programs.
The project investigates architectures, technical approaches, studies, processes, technologies, tools and proof-of-concepts across the following technical areas of identity management:
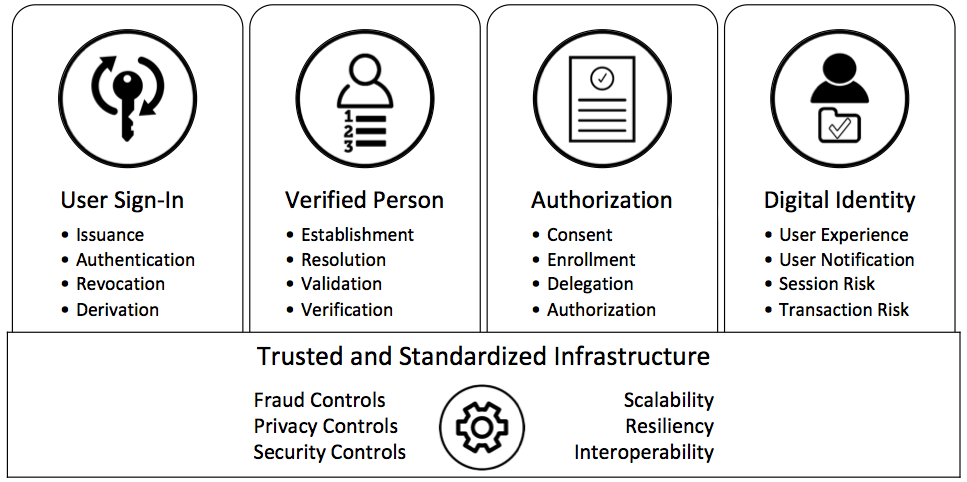
The project maps customer needs—gathered via regular customer and community engagement—against this model to drive project investments that mitigate identity management failures while ensuring a competitive marketplace.
Watch the Identity Management Project Video
Motivation
The project regularly engages with its customers and the community to identify customer needs not met with current technologies and understand the current state-of-the-art and practice in the identity management domain. As an R&D project, it “looks around corners” to ensure customers are not surprised by emerging trends or issues.
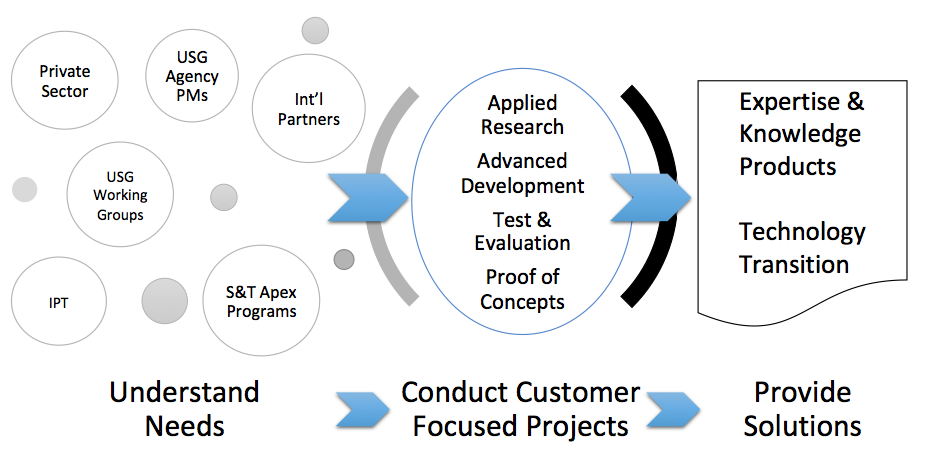
The results of the project’s ongoing customer and community engagement are used to develop and update its research agenda. This agenda drives its R&D of the capabilities needed to protect cyberspace in a manner that incorporates both security and privacy.
In cases where technologies do not exist or are immature, the project makes the necessary investments in applied research, advanced development, test and evaluation, and technology transition to ensure their availability to the Homeland Security Enterprise (HSE).
The project’s goal is to develop solutions that address customer needs and deploy or use them operationally via successful technology transitions.
Approach
The project starts each customer engagement with a discovery process in which it seeks to identify the pain/problem being experienced by the customer. Results of this process could identify one of two possible courses of action:
- A determination that technologies currently available in the marketplace can be used to solve the problem: In this situation, the project makes the necessary connections to the potential solution provider and supplies expertise for any necessary evaluations.
- A determination that a capability gap exists between the current state of technologies and what is needed to solve the problem: In this situation, the project makes the necessary investments to solve the problem and transition that solution so the customer has access to it through their existing acquisition mechanisms.

In either case, the project’s commitment is to provide a way forward for its customers without expecting them to be an expert in identity management or keep up to date on what technologies are available. The project helps its customers navigate through this whirlpool of confusion.
Performers
Center for Identity Technology Research (CITeR): CITeR is the National Science Foundation (NSF) Industry/University Cooperative Research Center (IUCRC) focusing on biometric identification and credibility assessment technology.
Digidentity: This performer is developing a capability that will use a number of effective identity verification methods that are not based on knowledge authentication approaches.
Exponent: This performer is developing the technology to perform secure communications and credential authentication over near-field communications (NFC) and Bluetooth using the standards-based, secure NFC Opacity protocol.
Gluu: This performer is developing the technologies and the trust framework needed for an emergency responder federation that will enable the introduction of a new mobile credential to communicate identity, skills and authorization in multijurisdictional disasters.
John Hopkins University Applied Physics Laboratory: This performer provides technical subject matter expertise and HSE and critical infrastructure customer engagement.
Lockstep Technologies: This performer is developing a capability to enable the transmission of professional credentials (attributes) in a range of use-cases via digitally signed attributes using mobile devices is being developed. This capability will assure the validity and provenance of attributes (e.g., qualifications and personal data), the sources of those attributes and the devices in which the attributes are stored.
Pacific Northwest National Laboratory: This performer is developing multiple projects in the areas of identity for nonperson entities and synthetic data toolsets.
Rutgers University: This performer developed and analyzed a solution for differentially private anomaly detection, which enables privacy-respecting screening capability to detect individuals, behaviors, areas or data samples of high interest. Also, in partnership with researchers at Xerox Palo Alto Research Center, the performer currently is developing a detailed technical specification for a privacy-preserving, active-learning architecture.
SecureKey Technologies: This performer is developing a mechanism to clearly separate login mechanisms from person verification and will implement a robust, secure and scalable ecosystem guided under Privacy-by-Design guidelines.
United Technologies Research Center: This performer is developing a continual, secure and user-friendly authentication platform that aims to overcome the limitations found in existing mobile authentication and application (app) access control techniques. The proposed technology will accomplish this by continuously analyzing the context around the device and by adapting application access decisions based on the perceived level of threats and context.
University of Washington Applied Physics Laboratory: This performer is working on multiple projects in the areas of verifiable claims issuance, compensating controls and the identity ecosystem mapping.
Resources
For the latest information about S&T Cybersecurity, visit the S&T Cybersecurity News, Publications, Videos and Events pages.
Publication & Video
Contact
Email: IDAM-E@hq.dhs.gov
