A new cutting-edge Control Environment Laboratory Resource (CELR) platform developed by the Science and Technology Directorate (S&T) and Cybersecurity and Infrastructure Security Agency (CISA) will help the U.S. Coast Guard (USCG) boost the cyber strength of our nation’s harbors.
Seaports play an integral role in ensuring the health of our economy. According to the National Oceanic and Atmospheric Administration’s Office for Coastal Management, $2.3 trillion of international trading is facilitated by our seaports, with roughly 1.6 billion tons of imported and exported goods being transported by almost 45,000 vessels every year.
To keep this vital infrastructure running smoothly, our nation’s more than 300 seaports rely heavily on sophisticated information technology (IT) (e.g. software, the cloud, and computer networks) and operational technology (OT) systems (e.g. industrial control systems, supervisory control and data acquisition systems, and terminal operating systems) for their daily operations. These systems are managed, accessed, and controlled via the internet, which makes them susceptible to “hacking, malware attacks, and other malicious online activities,” according to S&T Program Manager Eileen Rubin.
With funding from the Infrastructure Investment and Jobs Act, S&T, CISA, and the Pacific Northwest National Laboratory (PNNL) designed and implemented a laboratory-sized seaport platform that gives operators the ability to safely experience the effects of a cyber-attack and hone their threat hunting and cyber-defense skills.
“Cyber threats to seaport operations are a national security concern given our nation's dependence on seaports for the movement of products and material goods. A disruption, even of brief duration, could have cascading negative consequences at regional and national levels,” said CISA Industrial Control Systems Section Chief Alex Reniers. “Therefore, it is imperative that we take the time to understand the potential risks to seaport IT and OT systems that malicious cyber actors could exploit.”
Disruptions to a major U.S. seaport could affect shipments via road, rail, or pipelines for days or even weeks. Monetary damages could be in the millions or even billions of dollars and delay the arrival of critical supplies. These interruptions could significantly impact our economy and global supply chain, which is why the team is working to boost the online and physical security of this critical infrastructure so our frontline workers will be prepared to respond to any attempts to compromise their crucial services and related systems.
The new platform will ultimately be part of CISA’s Control Environment Laboratory Resource (CELR) program; be incorporated into CISA’s existing suite of OT security offerings; and serve as a training and research platform for USCG, Department of Homeland Security/Department of Defense partners, manufacturers, cybersecurity experts and researchers, and other seaport owners and operators.
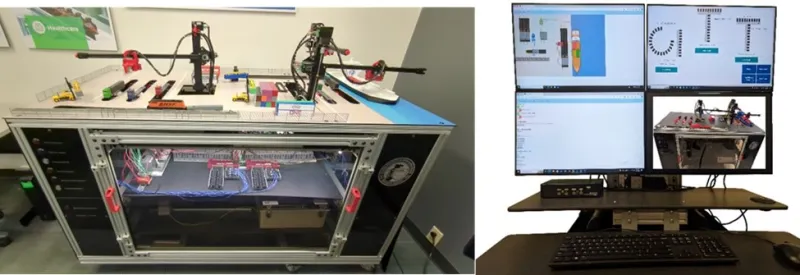
“CELR platforms are laboratory scale environments (about the size of a ping-pong table) that emulate critical infrastructure facilities and the processes, software, and hardware that they rely on in the real world,” said PNNL Senior Cyber-physical Engineer Scott Warnick. “They are designed to provide security professionals—alongside technical personnel, owners, and operators who may have limited exposure to cyber effects—with a safe setting to simulate and experience the effects of cyberattacks without real-world consequences.”
Stakeholders will be able to use the new CELR platform to study and analyze ‘attacks’ to discover IT and OT vulnerabilities and prepare to implement countermeasures that will detect, prevent, or mitigate these malicious online attacks. Nine additional CELR platforms are currently in operation at two national laboratory locations. PNNL operates four other platforms: a wastewater treatment system, a water treatment facility, a hydroelectric dam, and a freight rail platform which was also funded through S&T research and development dollars. Idaho National Laboratory (INL) operates five other platforms: an electric transmission substation; an electric distribution substation; a building management system; a chemical processing system; and a natural gas pipeline system.
“When CISA mentioned that the USCG’s Cyber Protection Team (CPT) identified the need to develop new training and testing tools for our seaports, we got right to work with subject matter experts (SMEs) in this field to build and implement a state-of-the-art seaport CELR platform,” said Rubin.
The platform is modeled after multiple seaports across the United States. It is designed to show users how the seaport’s various IT and OT systems and processes control daily operations such as the loading, unloading, and movements of containers between ships, trucks, and trains. Users can also simulate and observe the various effects of cyberattacks, and train to develop and implement appropriate countermeasures for these attacks.
The team recently hosted an online demonstration of the seaport platform for stakeholders to demonstrate functionality, including “normal” daily seaport operations, and also run scenarios that illustrate the potential consequences of cyberattacks.
Simulated cyberattack engagement scenarios are being developed in coordination with USCG CPT and are expected to be ready by next summer. From there, both the platform and simulated engagement scenarios will be made available to USCG CPT and others who want to access it for their own training or research purposes.
S&T and CISA are also looking at the bigger picture.
“Defending our nation’s critical infrastructure against threats and strengthening their overall cybersecurity is a high priority for CISA that requires vigilance, education, and collaboration from everyone in our field,” said Reniers. “And, since we have an entire suite of CELR platforms, one of our top priorities is to make all of them available to the cybersecurity SMEs, researchers, and owners and operators who would benefit from being able to use them.”
Over the next couple of years, S&T, CISA, PNNL, and INL look to spread awareness, build additional platforms, and increase access to the CELR suite, including equipping U.S. colleges and universities with their own test environments.
“We anticipate by doing this, it will increase accessibility to these vital resources and make it easier for critical infrastructure owners, operators, and staff to be more prepared to address potential cyberattacks against critical infrastructure in the future,” explained Reniers.
For related media requests, please contact STmedia@hq.dhs.gov.
