The DHS Science and Technology Directorate (S&T) Data Privacy project provides the Homeland Security Enterprise (HSE) the research and development (R&D) expertise and resources needed to enhance the security and trustworthiness of their programs by better aligning technology capabilities with individual and social expectations of privacy.
The project develops, tests and evaluates technical and knowledge solutions for the management of privacy threats and vulnerabilities that arise from socio- and technical policies and operations. The project’s R&D focuses on privacy risks related to:
- Connected sensor devices, mobile computing and sensor platforms
- Automation and autonomous systems
- The delivery of digital services
It reviews and updates these topic areas, which drive project focus and investments, using input gathered via regular customer and community engagements.
Motivation
Cyber-threats are rapidly shifting and privacy-related breaches are increasing in frequency and impact. The Data Privacy project is aligned with National Privacy and Cyber Security Research and Development strategic initiatives to develop a targeted set of research priorities to ensure that cyberspace is safe, trustworthy and prosperous.
Specifically, the project provides the R&D community expertise and resources to prevent, mitigate and recover from adverse effects of privacy threats and intrusions on privacy arising from information system policies and processing. This work includes mitigation of risks by engineering privacy-protecting systems, educating the public, and understanding behavioral, social, organizational and policy dimensions of privacy. S&T Cyber Security Division (CSD) is working to develop innovative solutions that ensure the protection of individual privacy is consistent with applicable law, policy and mission.
Approach
The project regularly engages with customers and the community to identify customer needs that cannot be met with current technologies and to understand the current state-of-the-art and practice in the data privacy domain. The Data Privacy R&D project actively is anticipating emerging trends or issues.
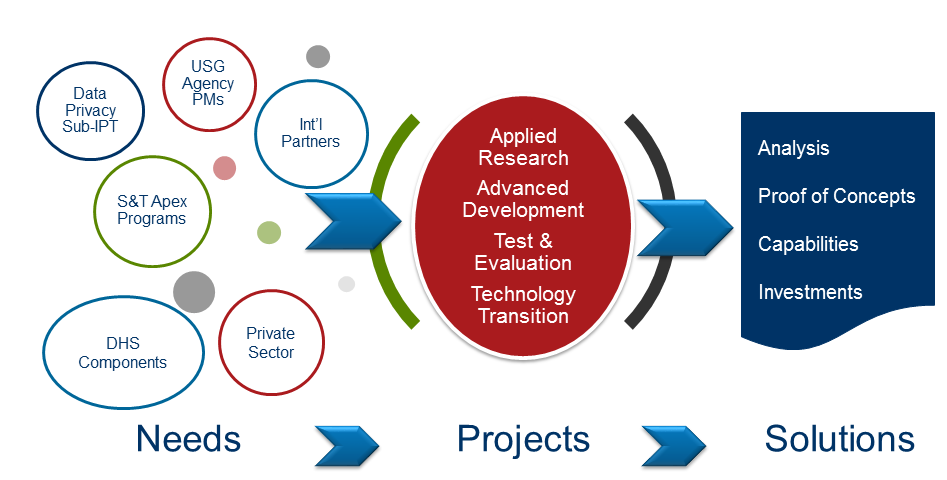
The results of ongoing customer and community engagement are used to develop and update the project’s research agenda. This agenda drives R&D of new capabilities that will protect cyberspace in a manner that incorporates both security and privacy.
In cases where technologies do not exist or are immature, the project makes the necessary investments in applied research, advanced development, testing and evaluation, and technology transition to ensure their availability to the HSE.
The project’s goal is to develop solutions that address customer needs and deploy them in an operational environment via successful technology transitions.
Performers
Northeastern University: Revealing and Controlling Privacy Leaks in Network Traffic
This effort enables the auditing and control of personally identifiable information (PII) leaks from mobile devices, web browsers and internet of things devices. This addresses the key challenges of how to identify and control PII leaks when a user’s PII is not known. A priori nor is the set of applications or devices that leak this information.
Raytheon: Privacy Preserving Federated Search and Sharing (PPFS2)
This effort combines advanced cryptography and policy reasoning to provide privacy-preserving federated search and sharing. It achieves this through a combination of established technologies: the ability to match encrypted content without divulging the search criteria (based on Predicate Based Encryption), selectively controlling access to clear text content (based on Attribute Based Encryption), and prior work on reasoning with machine-understandable privacy policies to decide whether a given information request is compliant.
Resources
For the latest information about S&T Cybersecurity, visit the S&T Cybersecurity News, Publications, Videos and Events pages.
Publication
National Privacy Research Strategy (PDF, 1,017.9 KB, 34 pages)
