The Next Generation Cyber Infrastructure (NGCI) Apex program (Cyber Apex), one of several S&T Apex Programs, addresses the cyber challenges facing our nation’s critical infrastructure sectors, enabling these essential entities to operate effectively even in the face of sophisticated, targeted cyberattacks. The program seeks to provide technologies and tools that will harden critical systems and networks. The United States critical infrastructure sectors have an immediate need for technologies that can adequately detect, defend, protect, restore and respond to sophisticated cyber-threats. The Cyber Apex program identifies, develops, tests, evaluates and deploys cutting-edge technologies to deter cyberattacks against critical infrastructure sectors.
Protecting the Nation's Cyber Infrastructure
Cyberattacks threaten national security by undermining information-dependent critical infrastructure. DHS has identified 16 critical infrastructure sectors, as designated in Presidential Policy Directive (PPD-21)—Critical Infrastructure Security and Resilience. Subsequently, S&T has identified three major challenges:
- Adversaries are infiltrating critical systems and networks without the knowledge of network owners/operators,
- The sectors’ understanding of the cyber situation is inaccurate, incomplete or only achieved forensically after an infiltration has occurred, and
- Network owners/operators lack strong ways to respond and mitigate the impact of adversaries on critical infrastructure systems while still allowing for the sectors to maintain adequate operating capacity.
The Cyber Apex program aims to reduce the vulnerability gaps of the nation’s financial industry’s critical infrastructure. The program’s overarching goal is to expand and provide benefits to other critical infrastructures by promoting and transitioning the technologies developed within the Cyber Apex program to them.
By identifying technologies and tools to defend against advanced adversaries when they attack U.S. cyber systems and networks, the Cyber Apex will concentrate on delivering capabilities identified by the financial sectors to address sector gaps.
- Network Characterization focuses on providing real-time understanding of a network, including the internal communication patterns of connected assets, to enable immediate anomaly detection and rapid response to cyber incidents.
- Data Protect focuses on ensuring the confidentiality, integrity and availability of sensitive data at rest, in transit, and/or in use.
- Advanced External User Authentication focuses on non-password-based, multi-factor authentication for external users, such as customers, business partners, and 3rd party suppliers.
- Dynamic Defense focuses on changing external and internal network layouts so they are harder for adversaries to probe, breach, and exploit, thereby increasing the economic costs for a potential attacker.
Customer and Stakeholder Engagement
The Cyber Apex Program Management Office (PMO) has established Cyber Apex Review Teams (CART) to define and prioritize requirements, plan and execute test and evaluation activities, and carry out the most appropriate methods of technology deployment and transition. The CART evaluates tools that can help the financial services sector defend against cyber-threats.
The CART is comprised of the U.S. Department of Treasury as well as financial services sector chief information security officers and cybersecurity experts.
Any financial services organization (FSS) can request to join the CART by contacting the DHS S&T program management office. For more information about joining the CART, please refer to the FAQ page or email: CyberApex@hq.dhs.gov.
Cyber Apex Technology Approach & Process
To address the current needs of the financial services sector, the program works with the sector to identify capability gaps and test, evaluate, and transition successful cyber technologies.
A key aspect of the Cyber Apex approach and process includes identifying the technologies to pursue to mitigate the identified gaps and routing them through one of two possible path; the Mature Technology Path, which utilizes a Consortium of technology vendors, and the Early Stage Technology Path, which leverages S&T's Silicon Valley Innovation Program (SVIP).
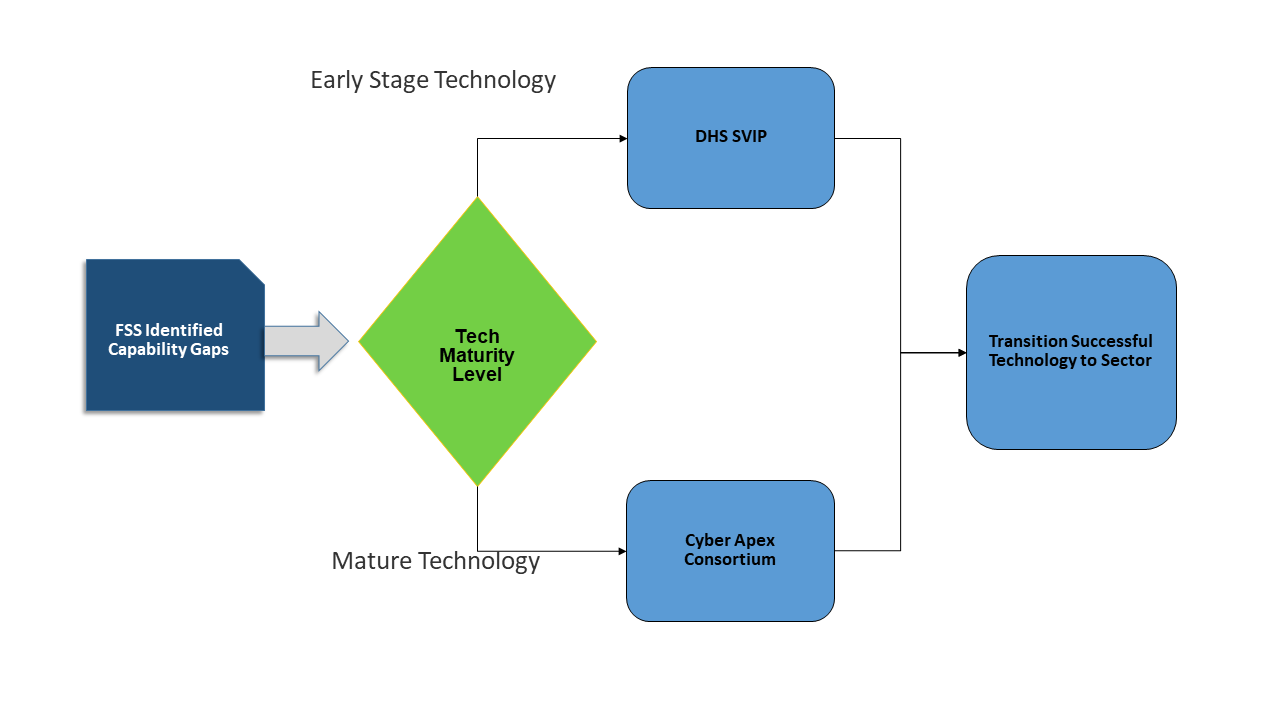
Technology can take two paths depending on the level of maturity.
Mature Technology Path: Consortium of Technology Vendors
When a capability gap is identified by the CART and mature technologies are available, the gap is turned into a project which is routed through the Mature Technology Path (also known as the Consortium). In these projects, the available mature technologies may require some development, integration with other technologies, or other adjustments in order to make it applicable to the FSS.
The Mature Technology Path utilizes a consortium, or pool of vendors, which is comprised of subcontractors to the OTA performer, in this case Cyber Apex Solutions. Consortium members will bid on proposals issued by Cyber Apex Solutions for each technology area and corresponding project effort.
To address the needs of the FSS, the Cyber Apex program will begin by identifying, testing, evaluating, and transitioning successful cyber technologies using a phased approach. The approach is designed to be a flexible, repeatable, and continuous process, which can be applied to each technology area (project) within the Cyber Apex program. The process includes Requirements Analysis, Technology Foraging, Metrics Development, Technology Selection, Solicitation Creation, Testing and Evaluation, and Transition to the FSS. The process is finalized once financial institutions adopt and transition the methodologies or technologies.

The Cyber Apex program uses an established, repeatable process to identify, test, evaluate and transition mature technologies to the FSS.
Early Stage Technology Path: Silicon Valley Innovation Program
When a capability gap is identified by the CART and little to no technologies are available, the gap is turned into a solicitation which is routed through the Early Stage Technology Path (also known as the SVIP path). The Cyber Apex Program leverages DHS’ Silicon Valley Innovation Program (SVIP) in order to reach out to the start up community.
Technology start-ups can apply to open solicitations.Awards are based on reviews of the applications by the Cyber Apex Program, SVIP, and other DHS cybersecurity experts. Awardees work with the CART to develop solutions in response to solicitations, which are tailored to the FSS community. The solutions are then piloted and transitioned to the CART for further testing.
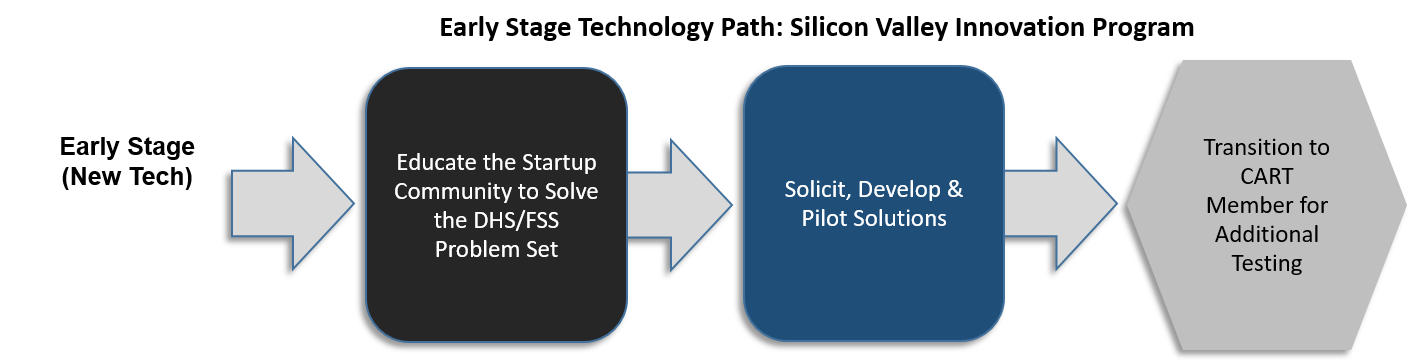
The Silicon Valley Innovation Program (SVIP) technology-development process
Current Projects
The Cyber Apex Consortium consists of technology owners and vendors who are able to submit solutions in response to projects directed through the Mature Technology Path.
Projects Under the Consortium
-
NetAware: The NetAware project focuses on the "timely discovery of cybersecurity events” and their contextualization in terms of network artifacts. Event detection may be performed at different levels (on a network sensor or aggregated at an operations facility, for instance) and is not limited to malicious activity directed only at network elements. It includes any cybersecurity activity that leaves residual information in network traffic. This excludes, for example, host-based security systems and mobile agents that perform detection at the device level, but could also include the fusion of networked aspects of these systems that may enhance the detection process.
-
NetIdentify: The NetIdentify project focuses on increasing overall network understanding to help organizations manage cybersecurity risk to systems, assets, data and functional capabilities. NetIdentify will help organizations understand the business context, the resources that support operationally critical functions, and the associated cybersecurity risks. This knowledge will empower organizations to focus and prioritize limited resources consistent with their risk-management strategies and business needs.
-
Next-Gen Analytics Management: The Next Gen Analytics Management focuses on advancing the state of technology that enables the sharing, discovery, characterization and comprehension of cyber-analytic methods and results. Shared analytic methods provide a means by which threat-hunters and analysts can increase the quality and the speed of discovery of fully actionable and relevant attack indicators. These shared analytic methods also support the normalization of outputs that enable DHS and Information Sharing and Analysis Centers (ISAC)/Information Sharing and Analysis Organizations (ISAO) to more easily discern cross-organizational patterns, vulnerabilities and indicators of compromise.
-
Data Protect: The DataProtect project focuses on ensuring the confidentiality, integrity and availability of sensitive data itself, whether at rest, in transit, or in use; protecting the networks, devices, and systems which house and process data; and addressing the ease of data access in the system design. This project will identify for testing (and possibly light development) solutions that help IT staff correctly configure, key, and coordinate mature COTS technologies that protect data residing on or traveling through enterprise computing resources. This will improve the correct configuration, key management, and coordination of current composed COTS technologies and increase overall effectiveness.
-
Advanced External User Authentication: The Advanced External User Authentication project focuses on non-password-based, multi-factor authentication for external users, such as customers, business partners, and 3rd party suppliers. As password-based authentication is at odds with normal human cognitive abilities, users tend to reuse passwords across many sites; this leads to the possibility of if one site is hacked and passwords compromised, the user’s accounts on other sites are often also compromised. While there has been progress in this area, current methodologies and technologies are insecure and/or slow.
Projects Under the SVIP
Projects routed through the Early Stage Technology Path go through the DHS S&T Silicon Valley Innovation Program (SVIP).
The recently closed Financial Services Cyber Security Active Defense (FSCSAD) solicitation focused on novel ideas and technologies to improve dynamic defense and assurance for protecting FSS critical infrastructure by using the following three capabilities:
- Intrusion Deception targets any portion or phase of an attack’s operations, including reconnaissance, propagation, exploitation, command and control, data manipulation, exfiltration, etc. Technologies may focus on deception for networks, endpoints, applications or data. Effective techniques will enable the long-term use of deceptive concepts in active cyber defense.
- Moving Target Defense is controlled change across multiple network and system dimensions to increase uncertainty and complexity for attackers by reducing their window of opportunity and increasing the costs of their probing and attack efforts.
- Isolation and Containment segments unfamiliar or malicious code before it reaches enterprise systems and study the behaviors to prevent future breaches. This technology attempts to force nefarious software to execute in an isolated, contained environment.
Open and Recently Closed SVIP Solicitation Calls
Cyber Apex is partnering with the S&T Silicon Valley Innovation Program (SVIP) in order to reach the start-up community. SVIP issued its first Innovation Other Transaction Solicitation (OTS)—HSHQDC-16-R-B0005—in December 2015. Subsequent solicitation have been issued in the following years. Current open solicitations can be found on the SVIP website. The OTS describes the overall program framework and eligibility criteria. Individual calls that describe specific technical areas and use-cases are issued under the Innovation OTS.
Open calls currently serving the Cyber Apex program:
No Current Open Solicitation Calls. Check back regularly for new open solicitation calls.
Closed calls that served the Cyber Apex program:
Financial Cyber Security Active Defense (FSCSAD): This solicitation closed in November 2017. Though new applications are not accepted, the Cyber Apex Program currently has performers (awarded prior to the solicitation close) continuing work on their projects under the FSCSAD solicitation.
Performers
Cyber Apex Solutions (CAS) is the Cyber Apex Consortium contractor. CAS conducts requirements gathering, technology foraging, metrics development, and end-user identification for the critical infrastructure technology gaps identified by the CART.
Def-Logix is a performer under the SVIP FSCSAD call. Def-Logix’s proposed solution will build on their current Department of Defense-funded/supported system—Entrap—and demonstrate a rule-chaining functionality for reduced false-positives and Cybox and STIX format of Entrap output. The current technology offers isolation and containment at the host level and offers moving target defense by redirecting system application programming interface calls to Entrap’s pre-call or post-call routines. Entrap works in both “active” mode to prevent attacks and “passive” mode to assist in forensic characterization tasks.
Heilig Defense is a performer under the SVIP FSCSAD call. Heilig’s proposed solution aims to increase the effort and resources a one-size-fits-all attacker requires by breaking the exploit kill chain. The solution will provide run-time protection against specific memory safety vulnerabilities to existing applications in a dynamic and randomized way.
NextiTech is a performer under the SVIP FSCSAD call. NexiTech’s storage virtualization techniques will be used to create multiple abstractions of a device to confuse potential attackers and provide many possible channels/ports that can be used to communicate with the device, while maintaining only one active/correct port. NexiTech randomly changes the configuration of the active port—similar to Internet Protocol (IP) or frequency hopping—to create a moving target defense.
StackRox is a performer under the SVIP Financial Services Cyber Security Active Defense (FSCSAD) call. The StackRox technology builds on container-native security software to automatically pause and contain applications that exhibit malicious behavior to reduce burdens on FSS cybersecurity resources.
Veramine is a performer under the SVIP FSCSAD call. Veramine’s proposed solution captures all security-relevant events related to processes, services, users, binaries, registry writes and network connections and then sends metadata about those events in real-time to a central server. The server analyzes those messages using rule-based and machine-learning augmentation.
Resources
For the latest information about S&T Cybersecurity, visit the S&T Cybersecurity News, Publications, Videos and Events pages.
