The Open-Source Software (OSS) Prevalence Initiative encourages private industry and cybersecurity authorities to adopt free and readily available standards-based protocols to mitigate the risks inherent in OSS.
The Initiative is funded by the Investment and Infrastructure Jobs Act (IIJA) (see S&T’s CISRR Program for more information) and is a component of a larger strategy led by the Cybersecurity & Infrastructure Security Agency (CISA) CISA Open Source Software Security Roadmap.
Work with Us
The OSS Prevalence Initiative is eager to partner with private industry and cybersecurity authorities!
To get started, email: OSS.Prevalence.Initiative@hq.dhs.gov
Areas for collaboration include, and are not limited to:
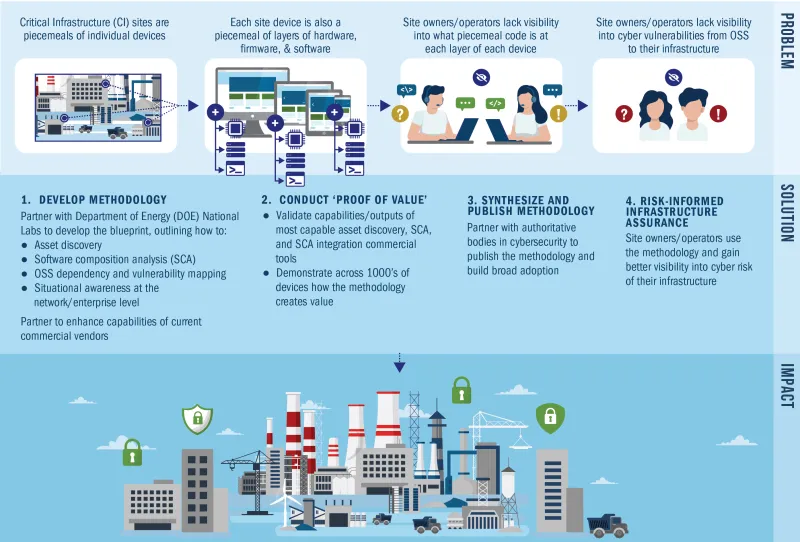
- Testing of asset discovery and software composition analysis (SCA) tools/techniques, we seek validations of tools to date and opportunities to partner on further testing.
- Technical feedback on our framework itself, we intend to hold upcoming engagements with others on our framework and need technical feedback on the techniques and procedures being used.
- Authoritative cybersecurity entities wishing to collaborate, endorse, and co-publish the final framework with S&T and CISA.
Current State of OSS
OSS is code that is freely available and can be readily used by anyone. Common usage includes:
- OSS that software developers can use to add features to their products, as opposed to re-rewriting the code.
- OSS for firmware for operational technology (e.g., widgets, smart devices, internet of things, etc.) that can be used as opposed to re-rewriting code.
The convenience of using OSS comes at the tradeoff of cybersecurity. The fact that everyone has access to the source code of OSS and a general lack of ownership of OSS (often termed "providence") makes OSS inherently vulnerable when used.
Recent and major OSS vulnerabilities found include:
- Log4J
- Kernal
The list of vulnerabilities known to have been proven to be exploited abounds:
Other components of CISA’s Open-Source Software Security Strategy include:
- Request for Comment on Secure Software Development Attestation Common Form
- Interagency collaboration and publications, such as via the Enduring Security Framework
- Principles for Package Repository Security
If you are interested in learning more about OSS and the current landscape of OSS, the Linux Foundation with Harvard University Census II Report is a reputable and well-written report on this.
There is much guidance available to network owners about what level of security they should be assuring their networks to, such as the Linux Foundations Supply-chain Levels for Software Artifacts (SLSA for short, pronounced “salsa”) or the NIST Secure Software Development Framework (SSDF). Additionally, the challenge grows when the current state of commercial-off-the-shelf (COTS) products in network assurance is that no single product can get a network owner to full network assurance, with many vendor capability claims having never been independently validated. DHS S&T seeks to develop the how for CI owners/operators to get to network assurance as per or the NIST SSDF or similar.